In this article James Tytler and Lawrence Copson analyse incident response data from 2023, unpacking what we witnessed, to reveal several surprising trends.
This is the final article in our special series looking at cyber incident response trends across 2023. All the articles have been wrapped together into the S-RM Cyber Incident Response Year in Review 2023.
Insights from 2023 in 60 seconds
Attacks on the rise
The number of organisations posted on ransomware and data theft sites increased by over 70% to a record high of 4,611 organisations
Tip of the iceberg
37% of the victims we responded to did not later appear on a leak site, despite not paying a ransom. Which, if applied to global data, suggests the total number of victims in 2023 is likely to be close to 12,500
fewer ransoms
Ransom payments decreased with payment occurring in only 24% of incidents
Secure the perimeter
External remote services are the most common way of getting into a network
A Fracturing ecosystem
Old foes remain but a swathe of new players has undermined threat actor reliability
Money in the mailbox
BEC incidents surged by 67% in 2023
Lying through lawyers
BEC gangs targeted law firms to intercept and tamper with payment processes
Small business, big Target
BEC attacks disproportionally impacted SMEs
But we have MFA?
MFA was bypassed in 29% of email account compromise cases
Attacks on the rise: Number of organisations posted on ransomware and data theft sites at record high
Despite all efforts to curb cybercrime, the tide has not turned. In 2023, ransomware and data theft gangs were far more active, with an increase of over 70% in the number of victims posted to dark web leak sites compared with 2022 (figure 1). 4,611 organisations, from charities to oil rigs, local libraries to international space stations, small farms to high tech household names, ransomware and data theft knew no bounds.
This spike in activity can be attributed to:
A shift to data extortion-only attacks: Several threat actors, such as Cl0p, shifted to semi-automated campaigns where they would exploit zero-day software vulnerabilities, steal data en masse without deploying ransomware, and then extort a large group of companies simultaneously.
Fewer ransom payments: Our data shows that there has been a small but notable reduction in ransom payments this year, which likely caused an increase in organisations appearing on leak sites.
Data dumps: We identified several new threat actors who are downloading data from previous attacks and then posting it on their sites to gain credibility and attract new members. For example, on 23 September the group LostTrust posted 52 victims on a single day.
The tip of the iceberg: Total number of victims likely closer to 12,500 in 2023
In 63% of our ransomware response cases, the name of the company was not later disclosed on a leak site. And, in 37% of our cases the company did not pay a ransom and still did not appear on a leak site. This suggests that leak site data is just the tip of the iceberg, as much as two-thirds of the scale of the problem is hidden below the water line out of sight. As such, we believe the total number of ransomware attacks in 2023 was likely closer to 12,500.
What is driving this discrepancy between the number of incidents and the number of leaks?
Threat actors lie: In several cases, our forensic investigation indicated that the threat actor had exaggerated their claims of data exfiltration.
Infrastructure takedowns: Law enforcement takedowns of major ransomware operations, such as RagnarLocker, Hive and – temporarily – BlackCat, may have interrupted access to stolen data, resulting in victims not appearing on the leak site even if the group did later resume operations.
Overheads: Hosting vast amounts of stolen data is expensive. Even the most prolific ransomware group, LockBit, appeared to experience issues related to unpaid storage, and failed to publish any new victim data during long periods in the spring and summer of 2023.
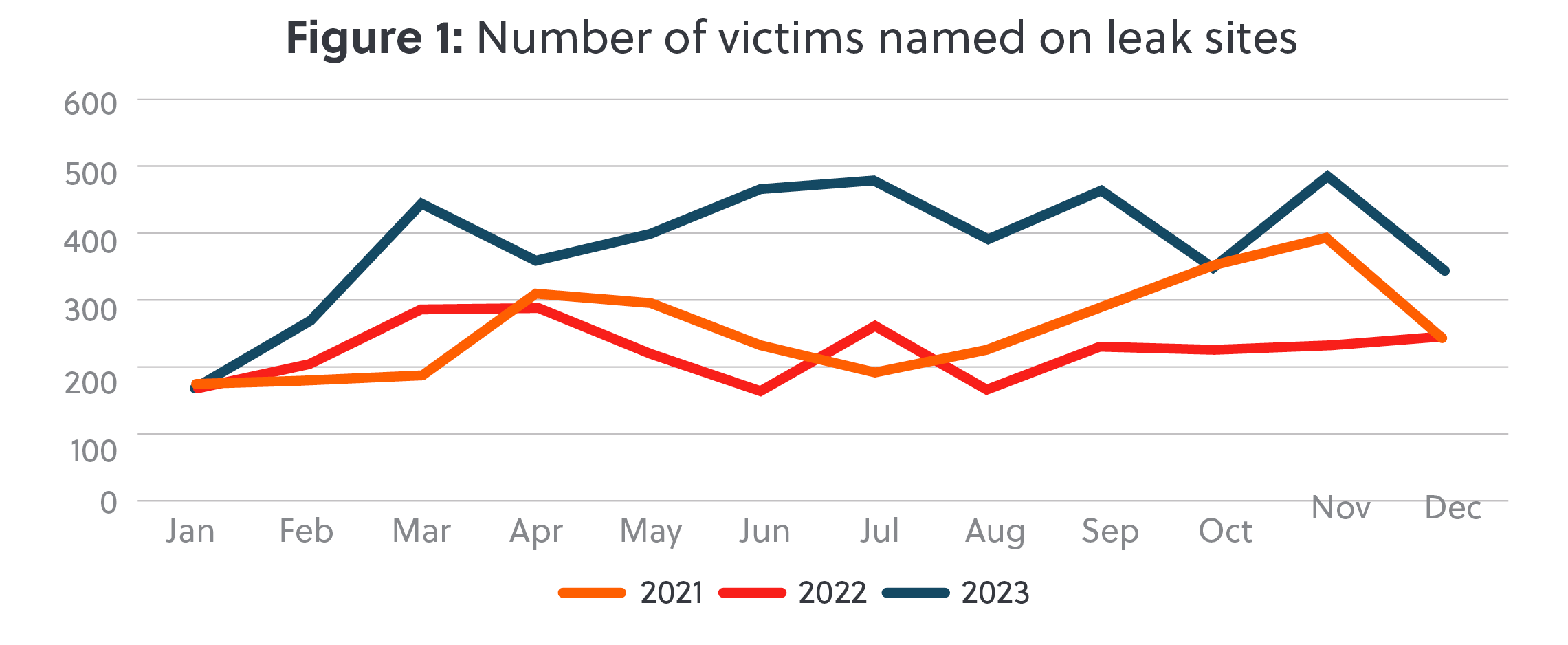
Data sourced from eCrime Threat and Risk Intelligence Services https://ecrime.ch/ [requires subscription]
Fewer ransoms: Ransom payments decreased with payment occurring in 24% of incidents
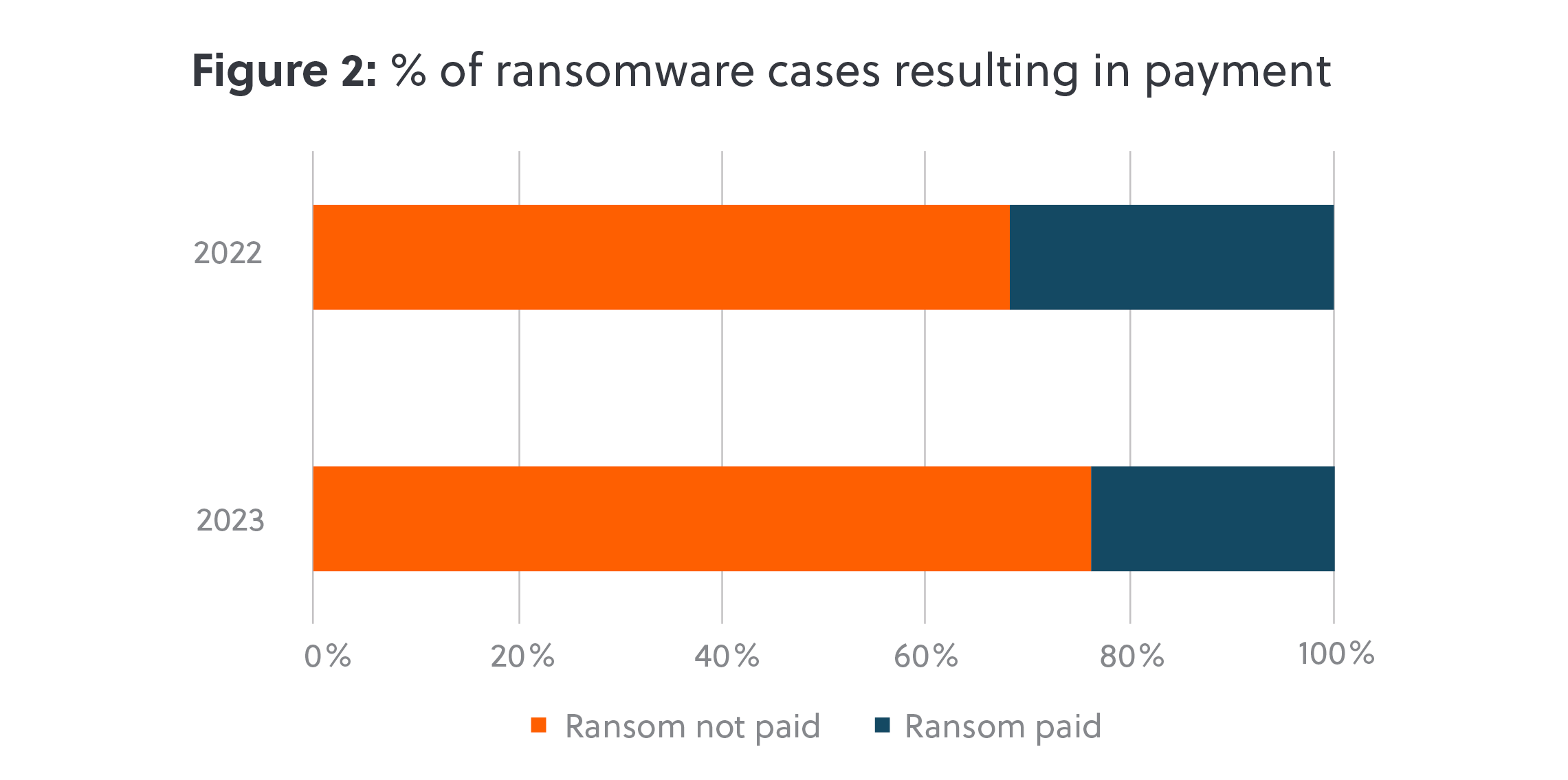
There are strong arguments for refusing to pay a ransom to cyber criminals. However, sometimes the damage done by threat actors is so great, or the data stolen so sensitive, that there is simply no other option but to pay if the business is to survive. Compared to the previous year, in 2023 we observed a small but notable decline in the rate of payment (figure 2). Of all the ransomware cases we responded to in 2023, a ransom was paid in 24% of cases. This was down from 31% in 2022. This may be in part due to the wider adoption off-site or cloud-based immutable backups, which can enable victims to recover without engaging with cyber-criminals.
Secure the perimeter: External remote services are the most common way of getting into a network
Exposed
In 2023, the most common method of entry for ransomware cases we responded to was via external remote services (figure 3), increasing from 35% in 2022 to 40% of all cases in 2023. From VPNs without MFA to insecure Remote Desktop Protocol, this category includes all internet-facing assets where we did not find evidence of a software vulnerability being exploited.
Zero days
The use of zero-day software exploits continues to drive incidents, the root cause of 30% of cases in 2023, up from 20% in 2022. Major contributors to this trend include the widespread exploitation of Citrix Bleed (CVE-2023-4966), Atlassian Confluence (CVE-2023-22518), and a critical Cisco IOS vulnerability (CVE-2023-20273).
Off the hook
Phishing was not a driver of major cyber incidents in 2023. Phishing was found as the method of entry in just 3% of our cases, compared with 16% in 2022. This decline is likely to be related to the takedown of major phishing botnets over the last few years, including Emotet, QakBot and TrickBot.

A fracturing ecosystem: Old foes remain but a swathe of new players has undermined threat actor reliability
LockBit leads
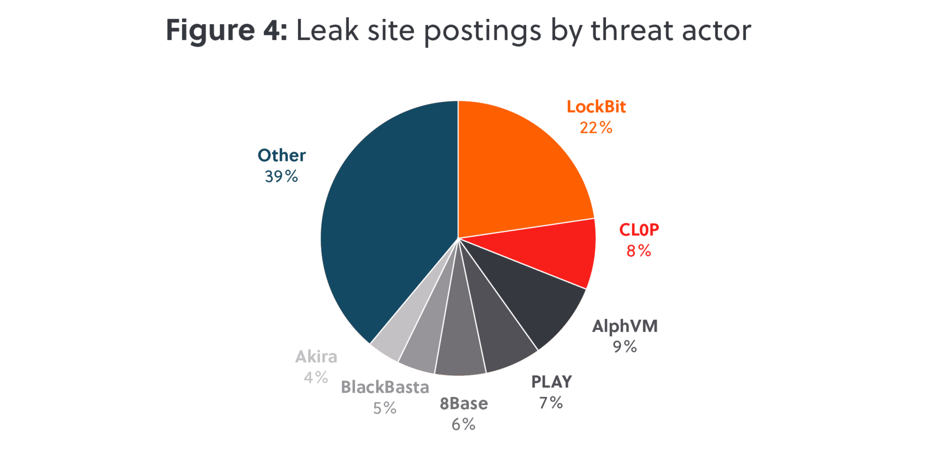
LockBit 3.0 continues to be most prolific ransomware group by a significant margin, responsible for 22% of leaks in 2023 (figure 4). Despite this prominence, LockBit had a turbulent year with data on their site regularly inaccessible, tension among their members, and new rules cracking down on ‘soft’ negotiators. In late 2023, LockBit’s members agreed on a new framework: The group will not accept ransom payments below 3% of their victims’ annual turnover, and will refuse to negotiate more than 20% from the initial demand. Only time will tell whether this is adhered to, and whether other groups follow suit.
Take the Cat out
The second most prominent group, BlackCat, demonstrated how difficult it is to takedown a large ransomware operation. Despite the FBI infiltrating BlackCat’s infrastructure in December 2023, the subsequent leak site takedown barely interrupted BlackCat’s operations, with new sites appearing days later. Despite efforts by law enforcement to ‘hack back’, this had limited success in 2023.
Spiders cross borders
While many prominent ransomware actors are believed to operate within Russia and the CIS, a hacking group referred to as “Scattered Spider”, is believed to be compromised of members in the UK and the US. This sub-group of BlackCat gained notoriety in 2023 when they staged attacks against Caesars Entertainment and
MGM Resorts.
Script kiddies love their new scripts
2023 represented a fracturing and de-professionalisation of the ransomware ecosystem. LockBit’s ransomware ‘builder’, or source code, was leaked and within weeks a swathe of amateur threat groups emerged using the opportunity to create small spin-offs, with no track record, no need to maintain brand reputations, and no long
term goals.
Old players, new brands
Lastly, we also observed several new threat groups who appear to be sophisticated rebrands of previous groups that disbanded, were taken down or disappeared over the last few years. This included 8Base who emerged from the disparate Phobos family; Hunters International who appear closely related to HIVE; Cactus and Akira who appear to be linked to the pro-Russian Conti gang; and there are new players, such as Rhysida, NoEscape, and the return of very old players, like Phobos and C3rb3r.
Money in the mailbox: BEC incidents surged by 67% in 2023
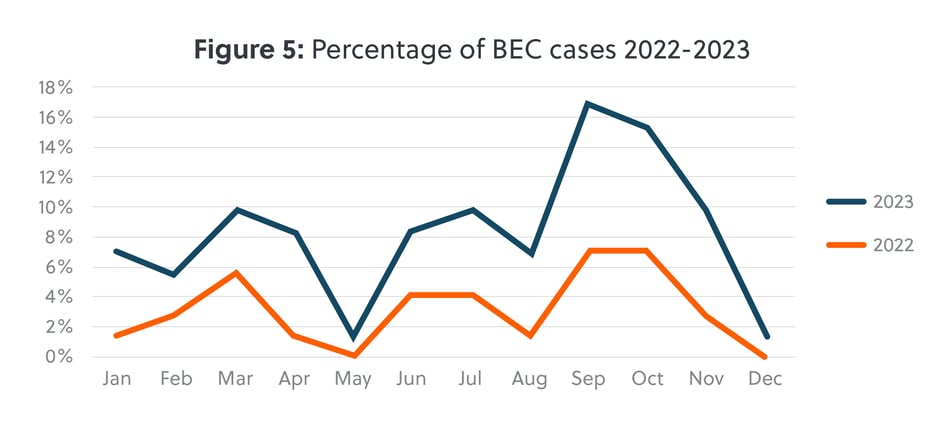
We saw a significant increase in Business Email Compromise (‘BEC’) cases in 2023 (figure 5), increasing by 67% year on year since 2022. Similar to last year, we observed a spike in activity in the autumn, after seeing a decrease during the summer months.
Lying to the lawyers: BEC gangs targeted law firms to intercept and tamper with payment processes
BEC gangs deliberately targeted law firms in 2023, accounting for 41% of all of our BEC cases (figure 6). Two key factors drive this trend: Firstly, law firms conduct a substantial amount of business through emails, and secondly, law firms are frequently included in processes where payment instructions are shared, with emails being the main platform for these exchanges. Both factors make law firms a uniquely attractive target for BEC gangs.
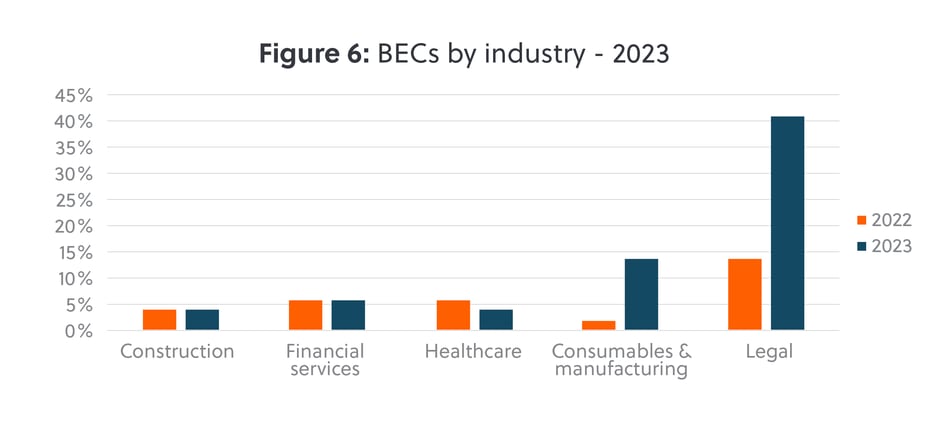
Small business, big target: BEC attacks disproportionally impacted SMEs
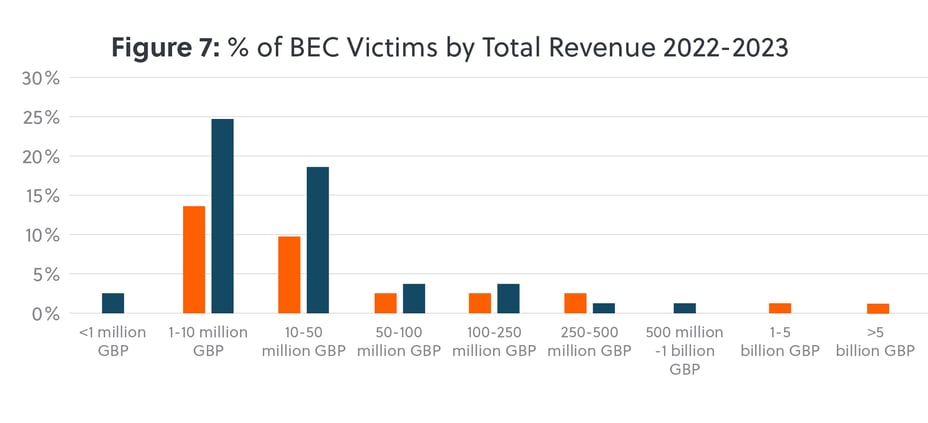
Small to medium enterprises were the primary targets, with victims with revenues between 1-10 million GBP almost doubling since 2022 (figure 7). Noticeably we saw a drop off in incidents impacting larger companies, as we observed more widespread usage of MFA, advanced email filtering solutions, and improved payment approval processes, all of which mitigated the impact of BEC attacks this year.
But we have MFA? MFA was bypassed in 29% of email account compromise cases
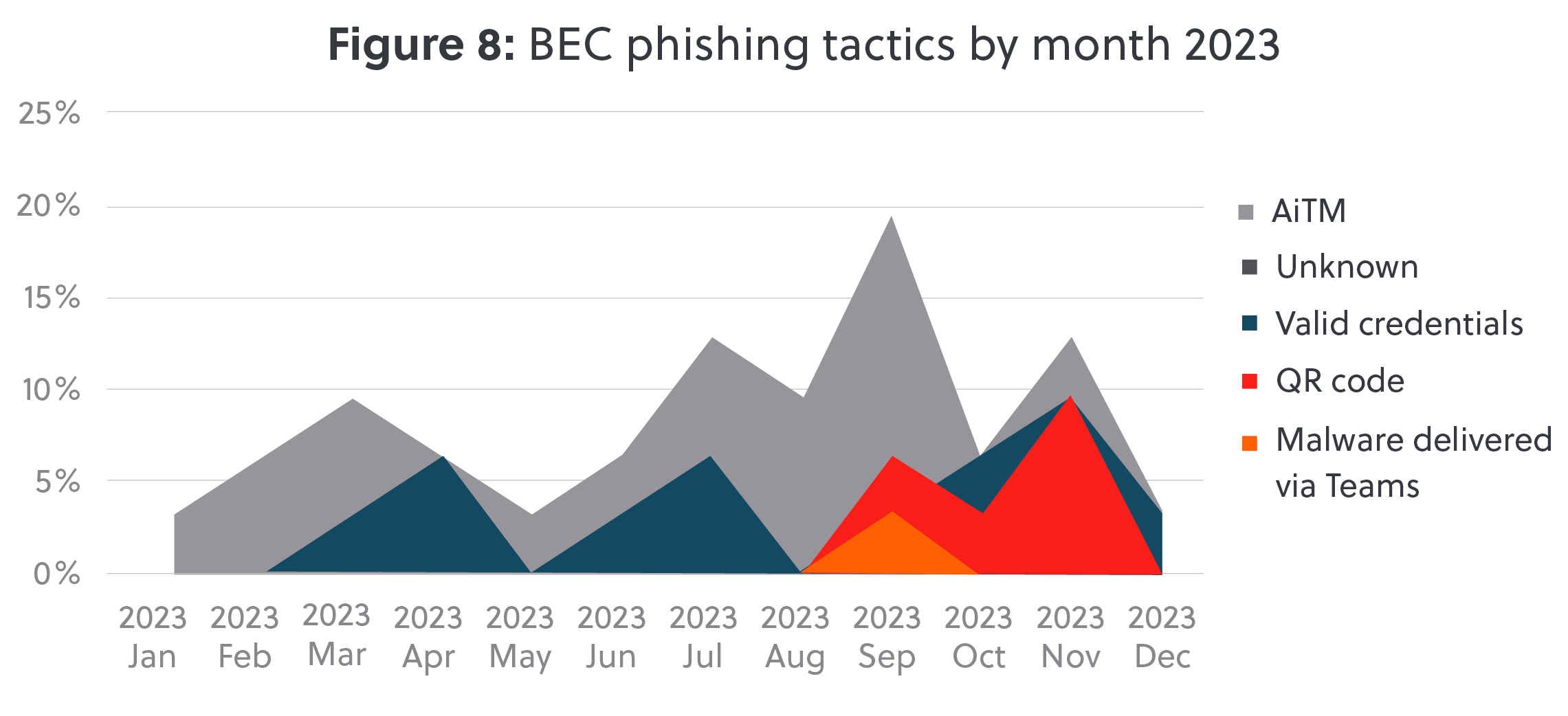
As defensive capabilities improved with the implementation of MFA setups to protect accounts, threat actors improved their offensive capabilities. In total 29% of the BEC cases we responded to, we detected the use of an Adversary in The Middle (AiTM) tactic to intercept and hijack data, called session cookies, which allowed BEC gangs to login without needing to know the user’s username, password, or provide a valid MFA code. In a novel trend, threat actors used malicious QR codes in 16% of S-RM’s BEC cases in 2023. We first observed this tactic in September 2023, and between September and November 2023, this new technique constituted a combined total of 42% of the phishing tactics employed by threat actors in such cases (figure 8).


-1-1.jpeg?width=121&height=121&name=MicrosoftTeams-image%20(11)-1-1.jpeg)



