In 2023 and 2024, the industry has observed an unprecedented level of law enforcement activity targeting major ransomware groups. In this special edition of the Cyber Intelligence Briefing, Melissa DeOrio examines the impact of recent law enforcement operations on the rate of criminal activity and explores what may be missing in the approach to reducing ransomware activity.
This February, the cybersecurity industry watched as the latest law enforcement effort, Operation Cronos, ensnared LockBit, a ransomware group once considered too big to fail. Internationally coordinated efforts against the group, along with last year’s operations on AlphV, RagnarLocker and Hive ransomware, seem to represent law enforcement’s growing commitment to penalizing those participating in the ransomware ecosystem. Despite these successes, however, it’s hard not to keep one eye on the still-increasing rate of ransomware attacks and wonder if all of this is even making a difference.
Measured success
In an ecosystem that relies heavily on anonymity and reputation, the introduction of unpredictability and breaches of trust has successfully added friction within these criminal syndicates. Ultimately, this increased concern about law enforcement infiltration and monitoring has prevented effective operations among many of them.
In Operation Cronos, “trolling” served this precise purpose. On the LockBit group’s own leak site, law enforcement announced arrests, unveiled the identities of affiliates, published details of seized cryptocurrency formerly held by the group and distributed key information about the group’s operations. The volume of the intelligence provided was intended to erode confidence in the idea that ransomware group affiliates can remain anonymous, and emphasised the group’s deepest insecurities.
To date the operation appears to be a success. A comparison of LockBit’s publicly reported victims for the first 12 weeks of 2023 and 2024 shows a decline in overall activity (see figure 1 below). Though the group was able to restore enough infrastructure to continue operating, and is attempting to develop the next iteration of the ransomware variant, it is likely that activity surrounding the strain will continue to taper off as affiliates abandon it for other alternatives.
Figure 1 LockBit 3.0 public victims
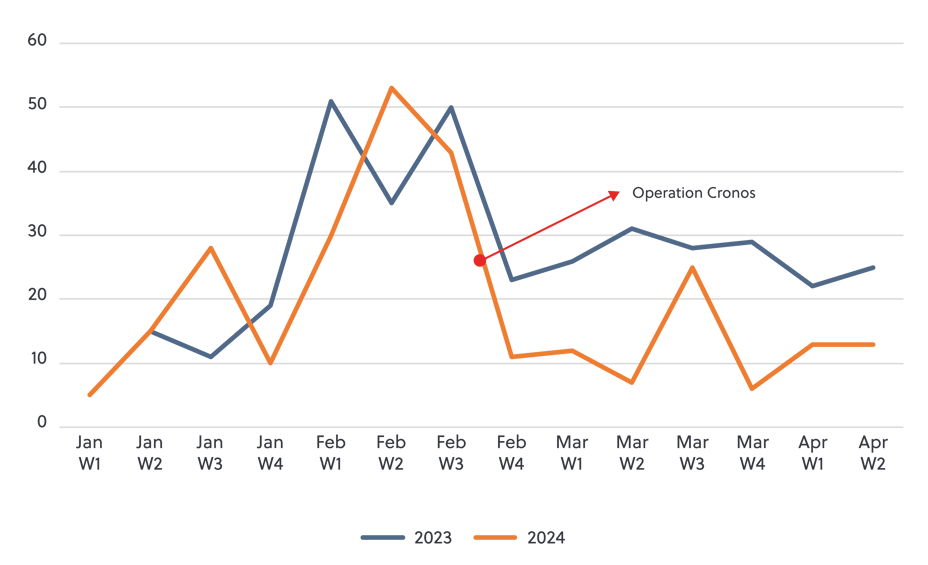
The expected dissolution of LockBit – and the recent dissolutions of AlphV, RagnarLocker and Hive – are great news, but if these operations are so successful, why is the overall rate of ransomware crime continuing to rise?
A lasting impact?
Figure 2 Law enforcement operations targeting ransomware groups 2021-2024
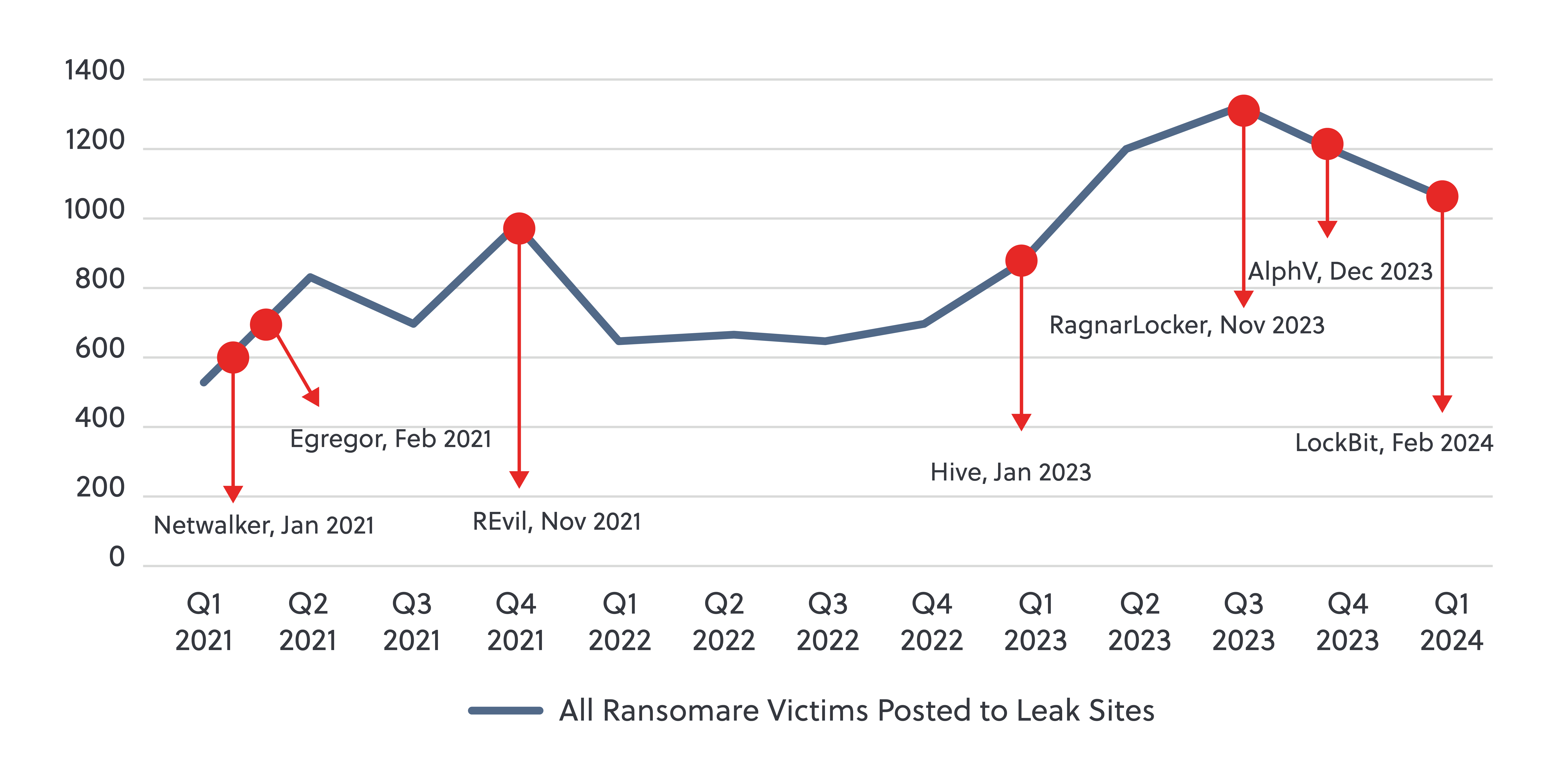
Plotting law enforcement operations against overall rates of ransomware activity since Jan 2021 (figure 2) provides insight into their impact on overall rates of activity:
Operations targeting Netwalker (Jan 2021) and Egregor (February 2021) ransomware could have been responsible for a dip in activity between Q2 and Q3 of 2021. However, any impact was only temporary, as activity reached an all-time high of 984 new victims on leak sites in Q4 2021.
Later in November 2021, law enforcement carried out mass-arrests of members of the REvil ransomware gang. This was followed by a precipitous drop in overall victims, but also coincided with the expected drop in activity that typically occurs during the Orthodox Christmas period. Although subsequent ransomware activity took a year to return to the level observed at the end of 2021, it is important to note that geo-political instability caused by the Russia-Ukraine War likely impacted this activity as regionally-based affiliates repurposed resources to target one another throughout 2022.
A long period without law enforcement activity during 2022 coincided with a gradually increasing rate of activity until the Hive takedown in January 2023. Though statistical modelling conducted by Chainalysis noted that this operation likely averted USD 210 million in ransom payments, the overall rate of ransomware crime appeared unaffected, steadily increasing to record-breaking levels over the coming months.
Operations targeting RagnarLocker (November 2023), AlphV (December 2023) and LockBit (February 2024) represent the most consistent law enforcement pressure yet applied to ransomware operators."
Operations targeting RagnarLocker (November 2023), AlphV (December 2023) and LockBit (February 2024) represent the most consistent law enforcement pressure yet applied to ransomware operators. Since the first of these operations, reported victim numbers have been steadily declining for the first time since 2022. Though it is too soon to tell, the compounding pressure of these concurrent operations, which is most likely to successfully inspire fear of punishment and impose higher costs to rebuild critical infrastructure, may prove to have a lasting impact. However, operations targeting singular groups instead of key enablers of the ecosystem, combined with funding limitations for future disruption operations, at least in the United Kingdom, may pose a challenge to maintaining this pressure, and offer groups time to rebuild.
Although law enforcement actions have coincided with temporary reductions in activity in the past, it remains to be seen whether the latest series will be enough to shift the tide.
Enduring challenges
Despite law enforcement’s increased efforts, cybercrime continues to represent a comparatively low-risk moneymaking opportunity. Those with rigorous operational security can continue to operate at little to no risk of identification, additionally the infrastructure and expertise required to participate in these activities at an affiliate level are increasingly minimal. Further, economic instability driven by widespread displacement, geopolitical turmoil and the aftermath of a global pandemic have made ransomware an increasingly attractive money-making opportunity, particularly for those living in areas where economies offer limited substantive alternatives.
Economic instability driven by widespread displacement, geopolitical turmoil and the aftermath of a global pandemic have made ransomware an increasingly attractive money-making opportunity"
The democratization of cybercrime facilitated by ‘as-a-service’ criminal wares has enabled low-sophistication “script-kiddies” to pursue criminal activities, and significantly disrupt organisations’ operations, with minimal investment or knowledge. The barrier to entry is being further lowered by the growth in initial access markets where specialists offer hard-sought initial access to organisations’ networks for as little as a few hundred dollars. We expect to see this activity continue to expand as artificial intelligence is more broadly adopted by cybercriminals and is utilised for the efficient identification of network vulnerabilities, automated penetration testing and more.
Further, traditional avenues of punishment through arrests, prosecutions and the imposition of sanctions require the attribution of real-life identities to those responsible for these crimes. Not only is attribution a time-consuming process, but even once they have been identified the location of these persons often presents additional challenges, such as elevated bureaucratic hurdles and limitations surrounding extradition. As a result, many of the most prolific and threatening actors continue their activities unabated.
Moving forward
Ultimately, the greatest challenge the government and security industry faces regarding ransomware is that it remains incredibly lucrative and there remains a lot of opportunity for money to be made. 2023 was the most lucrative year for ransomware on record, with groups raking in more than USD 1 billion in ransom payments, according to conservative estimates highlighted in recent research from Chainalysis. Increasing expansion of ransomware activity beyond western economies reveals that ransomware groups see a new frontier of prospective opportunities, making it difficult to imagine a world without ransomware.
Meaningfully addressing the ransomware threat long-term will require a broader toolkit; though these operations have achieved measured successes, periodic disruption of the largest groups will never impact the bottom-line on their own.
Meaningfully addressing the ransomware threat long-term will require a broader toolkit"
As part of this broadening toolkit, one component is clear. Increased partnerships between government agencies and public industry in the form of working groups and information-sharing channels can facilitate increased trust, meaningful dialogue and enable the development of practical solutions that support ransomware victims.
A desire to de-incentivize ransomware through the reduction of ransomware payments has inspired some to promote bans on ransomware payments. Though reducing the necessity of ransom payments is a critical part of the equation, it is crucial that related policies include avenues to support victims struggling to fund key cybersecurity controls or small-medium sized businesses often left with no other option to keep their business afloat.
Although there is no quick solution, recognising the necessity for a holistic approach is a crucial step in the right direction.




