Time is always in short supply during an incident response. In this article, Gavin Hull introduces Wiskess - his standout DFIR tool that automates the time-consuming steps of processing disk images and artefacts from Windows systems.
This article is the first in a special series on Cyber Incident Response. Our expert cyber team will release new articles over the next two months, culminating in an S-RM IR Bulletin in January 2024. Ensure you are subscribed to Latest Thinking to keep up to date.
When an organisation experiences a serious cyber incident, every minute counts. The amount of time it takes to go from the first response to complete remediation of an incident depends on the scale and impact of the breach, the response team and the technology being deployed. A critical objective in almost all cases is to figure out how the threat actor gained access to the network, and like a needle in a haystack, the investigation usually starts by collecting data from anything and everything left standing after the attack. As a result, incident response teams must process data from hundreds of endpoints as quickly as possible to plug the hole in the network, terminate any ongoing access to the network, and identify if any data has been exfiltrated.
This rush to answer key questions about the incident is coupled with other pressures. The response team must also support senior leaders within the impacted organisation who are desperately seeking to meet the demands of their stakeholders and are in the limelight, exposed from multiple angles. The pressures mount further with the legal and reputational ramifications of a breach and threat actors also pursuing to extort the organisation.
And within all of the melee, there is another balance at play. Responders want to get the answers, and get these answers quickly, but must investigate without compromising the validity of the findings.
The endpoint bottleneck
One of the major bottlenecks of an investigation is the process of endpoint data. Organisations typically have a collection of Windows endpoints, which require significant resources and time to process. One approach to address this issue is to have a larger team to process the data in parallel, which typically involves the following steps:
- Transfer of data to the response team
- Data put into a suitable format to process
- Data processed using multiple tools (one-by-one)
- Validation the data has been processed and finding valuable results
- Results into a timeline
- Backup the results and share findings with team members
The approach
This is a repetitive process and may result in the response team working unsightly hours. So, who’s available to analyse the results while the data’s processing? A manual approach to the process of incident response data becomes infeasible under the time constraints, pressures, and vast quantities of data. This is where Wiskess, an open-source Digital Forensics Incident Response (DFIR) tool developed and built by S-RM’s Gavin Hull, comes in to automate the incident response process.
Wiskess bringing speed, scale, and success
Wiskess automates the processing of disk images and triage collection artefacts from Windows systems. It does this with a pipeline involving six steps:
- Get the data – transfers data from cloud-based storage (i.e. AWS S3, Azure Storage), network drive, etc.
- Pre-process the data – structures the data into a suitable format for processing
- Process the data – covers the main artefacts of Windows system with parallel processing
- Enrich the findings – scans the data and findings with IOCs, yara rules and threat intel feeds
- Generate reports – timelines all results of the processing in a format compatible with visualisation tools (Elastic, Splunk, Timesketch)
- Store the results – results can be uploaded to cloud-based storage
The way of Wiskess
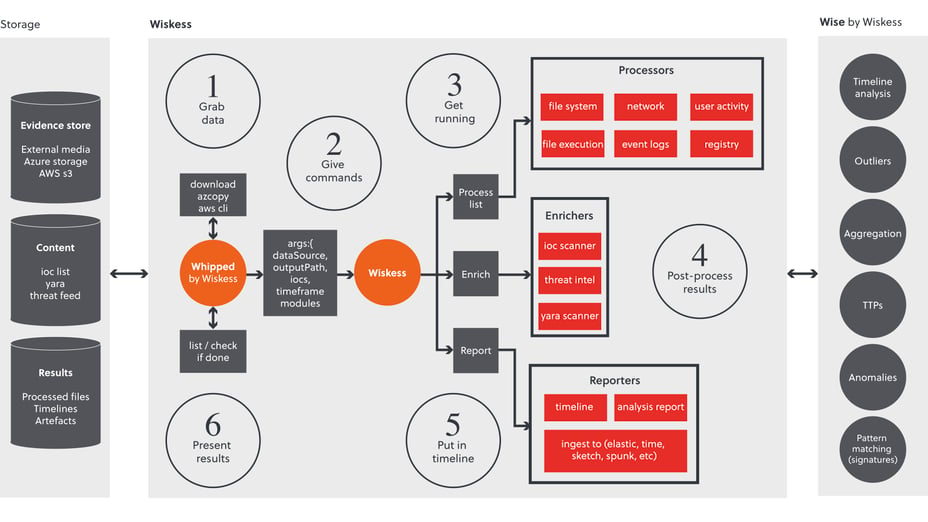
At S-RM we have used Wiskess for small and large-scale incidents with resounding success. It has taken the edge off an investigation, providing more resources for the analysis of the data. The tool has provided a standard approach to processing data, while it has also enabled responders to be flexible in their approach. Wiskess comes with a default configuration that covers most Windows artefacts, which responders can change to meet their needs – it accepts any command line-based tool.
Flexibility and speed are two advantages needed in investigations, where travelling to the site of the incident and setting up shop can take a large chunk out of the remediation time. Enabling remote response is now de facto in response teams. Instead of travelling, responders can advise local teams to install agents for data collection or to upload collections or images to cloud-based storage. Additional considerations are needed for incidents at scale, where hundreds of endpoints need processing. This is where the scalability of Whipped by Wiskess, the pre-process component, comes into its prime. Wiskess can be installed on multiple process machines, and then the data can be Whipped. Responders can easily setup Wiskess with the built-in 'setup' command and point it to the cloud storage.
This means answers to important stakeholder or regulator questions can be answered without the processing speed being a blocker. The built-in enrichment of the data has helped our response team to get quick wins of identifying threat actor tools, techniques, and procedures. The generation of a timeline that’s compatible with mainstream visualisation tools, including Elastic, Timesketch, and Splunk, has facilitated a team approach to analysing multiple data sources with a single pane.
Wiskess is currently available in two models:
- PowerShell version https://github.com/s-rm/wiskess_posh – designed with ease of use for developers
- Rust version https://github.com/s-rm/wiskess_rust – designed for better support of parallel processing
We have chosen to release Wiskess for other response teams to use, as we feel it will support the cyber security community to decrease the time to remediation and give more time for responders to track threat actor activity.
The GitHub repo has examples of how to run it.
Thanks to Wiskess, responders can put to rest the days of inefficiency, slow-processing and resource drains, and usher in an era of faster investigations, accurate results, and streamlined workflows.



